Introduction
Security life cycle is responsible to what information and system need to be protected in an organization. Today, data is the motherlode for criminals. Organizations now employ data security software to keep their data protected. Data typically needs to move freely between customers, organizations, and trading partners. This will create complexities and vulnerabilities into processes for many organizations.
Life cycle security let us to achieve end-to-end encryption and protect our data. Protecting data one of the problem is visibility which trigger cybersecurity weakness,
Data Security is a blue print to help organizations identify where their data is vulnerable, and where gaps could lead to data breach
Data Security Lifecycle Phases
The data security phases consists of the following 7 stages
- Capture*
- Store*
- Analyze
- Use
- Publish
- Archive
- Purge
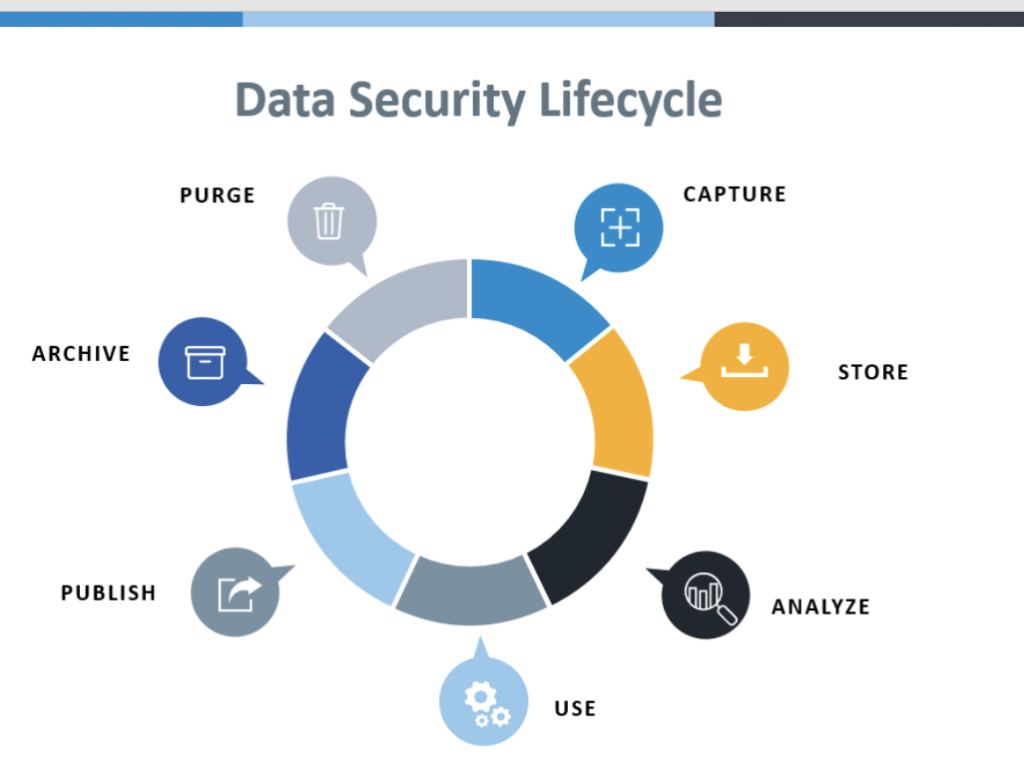
Figure 1.1 : – Data Security Lifecycle
Capture
It is. a phase that organization starts to intake or collect data. In this phase organization should implement a gate keeping strategies to control what types of information are you are collecting and storing, and to guard against malicious files.This will make sure that the data collected are legitimate. As the data is getting collected, make sure to address the sensitive of data ignorer to classify data as high and/or less sensitive to provide data privacy.