Introduction
It is an authentication method that enables users to securely authenticate with multiple applications and websites by using just one set of credentials. Most of us use different credential information for accessing different set of application. This is a big headache to remember all the credential to access different application.
In addition to that , most credential at the time of set up made of a combination of strong set of characters letter, numbers and special characters. Therefore it is super difficult to remember all the different types of credential. This will make the user to remember each credential through the following ways which are not a good solution
- A PC sunflower – A pc with a lot of stickers having a credential[username, password]
- Store the credential in a file / notepad, excel – which are ensure.
- Using the same password for all types of credentail.

Therefore the alternative solution is using SSO that is creating a trust relationship set up between an application, known as the service provider, and an identity provider, to let the authentication done in OneLogin.
figure 1.1 – Insecure way of storing credential
How does SSO Works
As it is stated above in the introduction, the SSO let us to implement one login /credential to access different types of application. For such implementation the service provider and identify provider should create a certificate and exchange the certificate to authenticate the user in the application.
The certificate can be used to sign identity information that is being sent from the identity provider to the service provider so that the service provider knows it is coming from a trusted source.
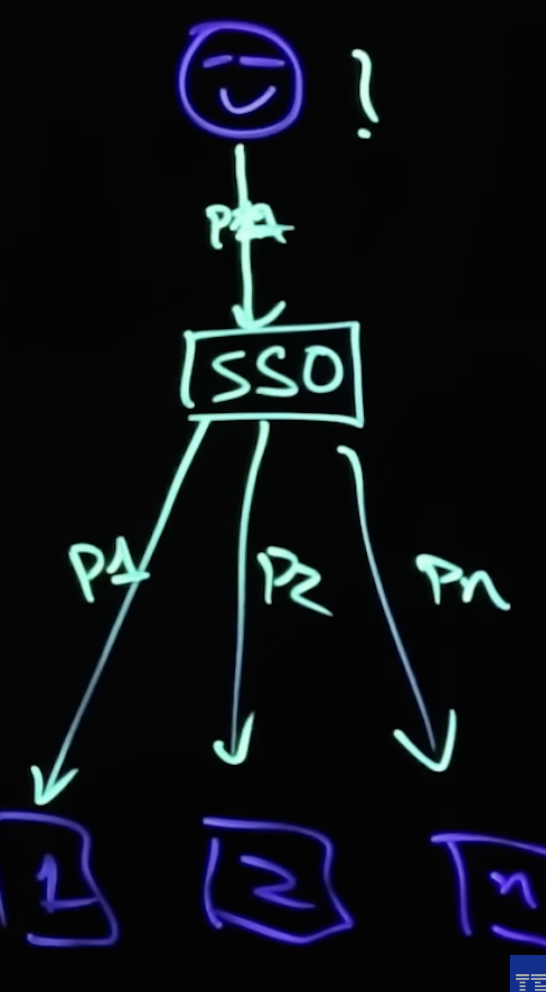
figure 1.2 – SSO – Single Sign On
How a user Authenticated in SSO – Single Sign On
A user to access an application through a single sing on could pass the following steps. The steps are considering that the identify provider and service prover already established a trust relationship. This means that as the user authenticated with the identify provider , the serve provide can let the user access its services. so let see the steps
- A user browses to the application or website they want access t
- The Service Provider sends a token that contains some information about the user, like their email address, to the SSO system. in line with this the Identity Provider, as part of a request from the service provider start to authenticate the user. [ if the user already authenticated , the service proivider grant access for the user or else the user will be asked to provide a credential – username, and password]
- once the identify provide validate the credential and send a token to service provider confirming a successful authentication
- This token is passed through the user’s browser to the Service Provider.
- The token is received by the Service Provider is validated according to the trust relationship initially made/configured with the identify provider.
- Then finally the user is granted access to the Service Provider
MFA – Multi-Factor Authentication
This is an additional layer that is supposed to be in-placed to protect SSC The implementation of MFA will be adding user telephone, or bio-metric information so that as the user access through a single sign on, it will be redirect to provide also MFA information as a confirmation of the last phase in the authentication process.
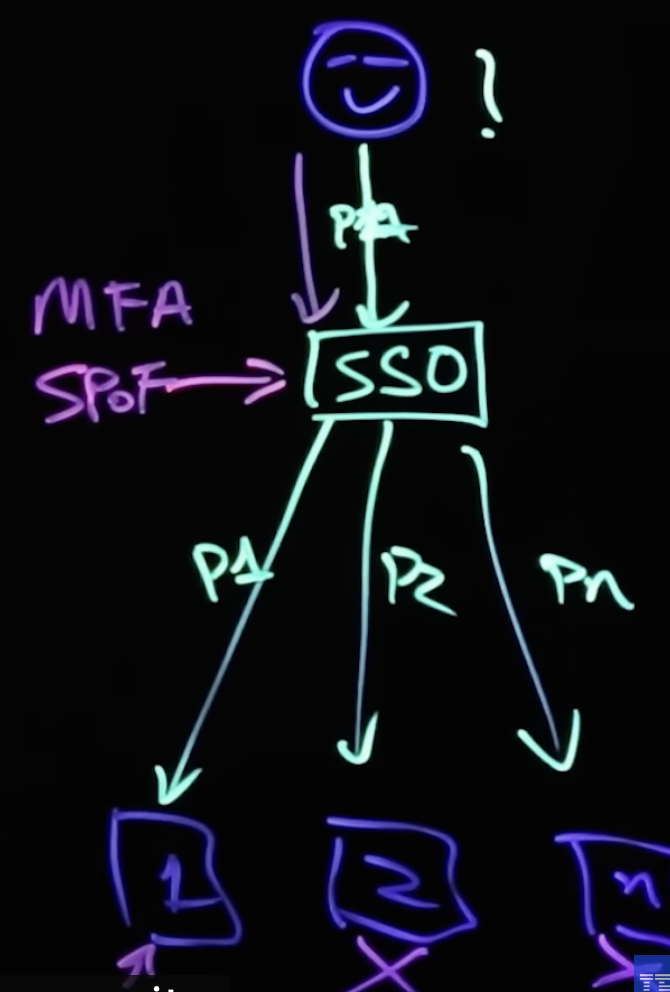
figure 1.3 – SSO+ MFA
Advantage of using SSO + MFA
The following are the possible solutions and advantage that SSO brings to a table
- More secure
- Cost effective / This will reduce the amount of time that users are requesting to re-set their password.
- Create as well better user experience./ user need to remember only one password